Saturday, November 14th, 2015
| Time | Event |
|---|---|
| 12:00 – 12:45 | Registration |
| 12:45 – 13:00 | Opening Ceremony BSides Winnipeg Organizers |
| 13:00 – 13:30 | In-Home Robots: Giving Intruders a Helping Hand Brittany Postnikoff & Daniel Rea |
| 13:30 – 14:00 | Rust: Bad for your Car, Good for your Code Base Ben Bergman |
| 14:00 – 14:30 | Coffee Break Catered by the King's Head |
| 14:30 – 15:00 | Interactions Between Deep Freeze and Active Directory Meako Marlow |
| 15:00 – 15:30 | Detecting and Preventing Phishing Attacks with DNS Reconnaissance Mike Saunders |
| 15:30 – 16:00 | Y U No Bild Bridge Higher? Christina Penner |
| 16:00 – 17:00 | Dinner Catered by the King's Head |
| 17:00 – 17:30 | Privacy in Data Management Noman Mohammed |
| 17:30 – 18:00 | Telephony Denial of Service Attacks and Spam: What is it, and how could we meet this threat? Cian Whalley |
| 18:00 – 18:30 | Feasibility Study: Authenticated PC Firmware on the Cheap Mark Jenkins |
| 18:30 – 19:00 | TSA Luggage Locks: Details, Flaws & Making the Best of a Bad Lock Adrian Crenshaw |
Sunday, November 15th, 2015
| Time | Event |
|---|---|
| 12:00 – 12:30 | Hardware Hacking 101: Erasing ThinkPad Supervisor Passwords Alex Weber |
| 12:30 – 13:00 | The Challenges of System/Network Segmentation in an Enterprise Oleksiy Vasylyuk |
| 13:00 – 13:30 | Modern TLS in the Enterprise Sean Cody |
| 13:30 – 14:00 | BGP, some Python, and a DB Theodore Baschak |
| 14:00 – 14:30 | Coffee Break Catered by the King's Head |
| 14:30 – 15:00 | Let Go of the Tools Tim Jensen |
| 15:00 – 16:00 | Basics of Radio Waves and SDR Colin Stanners |
| 16:00 – 17:00 | Dinner Catered by the King's Head |
| 17:00 – 17:30 | Network Configuration Management Zoë Rose |
| 17:30 – 18:00 | Fun With WOW64: Abusing Long Mode Transitions in Exploit Payloads Darren Kemp |
| 18:00 – 18:30 | Meaningful Measurement: Feeding the Cyber FUD Monster Ian Trump |
| 18:30 – 19:00 | Closing Ceremony BSides Winnipeg Organizers |
TSA Luggage Locks: Details, Flaws & Making the Best of a Bad Lock
Adrian Crenshaw
Every lock picker knows that the TSA approved Travel Sentry/Safe Skies locks are garbage, but if you don’t want your normal checked bags to have their locks cut off, there are only so many options. While this knowledge is common to lock sport folks, the average traveler is mostly unaware of it. This talk will cover the 7 master keys used by the TSA, non-destructive attack methods to open the locks, efforts to reproduce the master keys by reverse engineering the locks, and what TSA approved locks are the best of a bad situation.
Adrian is an infosec geek that records many videos from conferences. He's known for running Irongeek.com.
Hardware Hacking 101: Erasing ThinkPad Supervisor Passwords
Alex Weber
Most laptops can have power on and BIOS passwords, and they can be cleared by taking out a coin cell battery or placing a jumper on some pins. Lenovo and IBM business-class laptops famously have a special password that cannot be reset so easily. This talk will cover passively sniffing and erasing this password with inexpensive hardware hacking tools.
Alex is an ex-Director of SkullSpace. His day job is at Tenable Network Security working on the Nessus vulnerability scanner. Alex has a hobbyist interest in cryptography, compilers, and application security.
Rust: Bad for your Car, Good for your Code Base
Ben Bergman
Most programming languages make you choose between control and safety. Rust was designed to give you the best of both worlds with compile time checks for memory safety issues. Dangling pointers and race conditions are a thing of the past!
Ben is a University of Manitoba Computer Engineering graduate, a software developer at Tenable Network Security, and an electronics hobbyist (creator of the world's smallest Nintendo controller).
In-Home Robots: Giving Intruders a Helping Hand
Brittany Postnikoff & Daniel Rea
This presentation will outline security vulnerabilities present in home-use robots. This will be followed by a discussion of the security, privacy, and ethical implications of in-home robots, the Web-based applications used to control them, and the possibility of a future where we face more threats from inside our home than out.
Brittany is an undergraduate computer science student focusing on Human-Robot Interaction and security at the University of Manitoba. Her previous diplomas, Business Administration and Business Information Technology, are from Red River College, where she studied a blend of management practices and Web/application development techniques. Her security knowledge is rooted in SkullSpace (Winnipeg’s Hackerspace), yearly pilgrimages to DEF CON and other hacker conferences, and three years of industry experience.
Daniel is a Ph.D. student in Human-Robot Interaction at the University of Manitoba. His current research is about learning how to integrate techniques developed in video games into robot control interfaces. His M.Sc. is also from the University of Manitoba, where he developed a method to create movement AI for video game NPCs without programming. He is a frequent visitor at the Igarashi lab at the University of Tokyo, ATR robotics lab in Kyoto, and the iLab at the University of Calgary.
Y U No Bild Bridge Higher?
Christina Penner
How does the technology you work with change society? How does society change the technology you work with? These two questions are paramount to a flourishing field of academic study: Science and Technology Studies (STS). This presentation will ask you to consider the political implications of the work you do, and also encourage you to be aware of the social and political pressures that determine how, where and what you work on. The presentation will provide an overview of the field of Science and Technology Studies including both current and historical examples of the symbiotic and political nature of technology and society.
Christina Penner is an Instructor 2 in the Department of Computer Science, Faculty of Science and teaches first-year programming courses, third and fourth-year courses in Technical Communication, and a third-year course in Professional Practice. Ms. Penner also holds a M.A. in English from the University of Manitoba. Her first novel, Widows of Hamilton House. Enfield and Wizenty, Winnipeg, MB. 2008 won the Manitoba Day Award from the Association of Manitoba Archivists and was nominated for three literary awards: the Carol Shields Winnipeg Book Award, the Eileen McTavish Sykes Award for Best First Book by a Manitoba Writer and the John Hirsch Award for Most Promising Manitoba Writer. She has won several grants from the Manitoba Arts Council in support of her writing. Christina is working on her second novel, Kate's Pharmacy, which uses text messages, social media and Web-based interactions to solve a mystery while the novel investigates and exposes how technology fosters and changes relationships.
Telephony Denial of Service Attacks and Spam: What is it, and how could we meet this threat?
Cian Whalley
We are all familiar with DOS and DDOS attacks, but what is a TDOS attack? TDOS attacks are on the rise world-wide, and there is little that can be done about it today. With the cost of VoIP services dropping, and the rise of black hat VoIP services in countries that ignore law enforcement requests, we are experiencing a rise in Telephony spam, much like email did in the late 90's. This talk will go over the architecture of an attack, and explain in detail how it works, along with a live demo where Cian attacks a volunteer audience member's cell phone. What is to be done about this threat? Do we give up on the PSTN and admit defeat, or do we learn from the tactics of the past where we learned how to mitigate the mass volumes of spam world wide? This talk will conclude by outlining a high level plan for Canada to combat this threat.
Cian is a telecommunications professional known for evolving legacy TDM networks into next-generation voice over IP (VoIP) networks. He is an advisor to the CRTC and other telecommunications groups.
Basics of Radio Waves and SDR
Colin Stanners
Software-defined radio (SDR) technology has opened up the far reach and opportunity of radio waves to the flexibility and low cost of software. This talk provides a quick overview of radio theory, SDR architecture, popular hardware and software platforms, and some common projects.
Colin lives in Winnipeg, and has extensive experience in the design, installation, and support of long-distance wireless networks. He spends his 'free' time working on various networks, PCs, security camera and card access systems for SMB customers and volunteer projects, and maintaining two cats.
Fun With WOW64: Abusing Long Mode Transitions in Exploit Payloads
Darren Kemp
This talk will cover some of the basics of the Windows on Windows (WOW) subsystem, noting some more subtle behaviours and how they can be abused by an attacker. We will walk through the process of building a functional payload which bypasses a number of common exploit mitigations, explaining some of the common pitfalls along the way. Finally, there will be a demonstration of a live demo of the bypass in action using a real-world exploit.
Darren is a Security Researcher with the Duo Labs team bringing over a decade of professional experience in the information security industry. Darren specializes in vulnerability, malware analysis and software reverse engineering. Prior to Duo Darren held roles in application security consulting, threat intelligence, and helped develop advanced crash dump analysis tools. He is also that guy with the 'ginger' badge at REcon.
Meaningful Measurement: Feeding the Cyber FUD Monster
Ian Trump
Fear, uncertainty, and doubt (FUD) has become a staple in the cyber-attack measurement and reporting diet. Be it sensationalist and hyperbole-filled language, or the lack of any meaningful and consistent measurement methodology, the end result is the same: zero clarity concerning an already complex subject matter which serves to continue rather than counter the cyber-crime threat. The public discussion (via media reports) and business insight (through myriad methodologies of mis-measurement) need to be better framed if we as an industry are to truly confront the growing and increasingly expensive problem of cyber-crime. Who the criminals were is of less import than how they got in; compromise indicators are more valuable to other businesses than the financial cost to that particular victim. The measurement metric dial has moved too far towards attribution and needs to be reset to prevention and a business-based analysis of risk once more.
Ian is a long-time SkullSpace member and former director, the CTO of Octopi Managed Services, the Security Lead at LogicNow, a BSides London Presenter, Interop, and Cloud Security Europe Presenter.
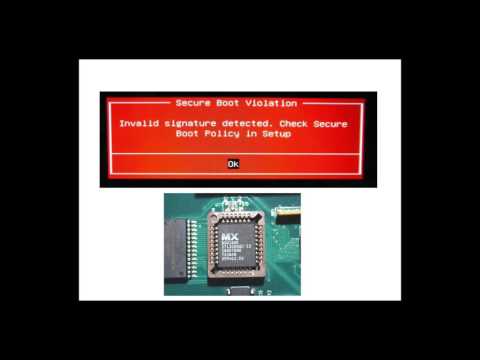
Feasibility Study: Authenticated PC Firmware on the Cheap
Mark Jenkins
If you want to authenticate that a PC's firmware and boot loader are unaltered, hardware based solutions such as trusted platform module (TPM), Intel boot guard, Intel Platform Trust Technology (PTT) and AMD equivalents probably come to mind. Such contemporary hardware features may not be affordable, available, or trusted. An approach that works on older computers acts as a hedge, available if hardware makers become malicious and as additional competitive discouragement for them to do so and undermine general-purpose computing as we know it. We assess the feasibility for the following soft approach: 1) A special boot verifier is loaded from secondary storage by firmware 2) Over a local connection, a trusted second computer sends random parameters for a difficult hashing problem to the boot verifier, this problem requires the contents of firmware and boot relevant parts of secondary storage as inputs and demands the entirety of RAM be utilized 3) Solutions at particular checkpoints to the hashing problem are transmitted to the second trusted computer 4) The secondary computer verifies not just the correctness of all solutions, but their timing of transmission against an established benchmark for the machine tested. For older x86 hardware without virtualization extensions (where hardware access for transmission can introduce a significant performance penalty), the idea is that any attempts at virtualization or hiding a malicious payload with the help of paging will show a detectable performance hit on timing. The threat model is an attacker who can only alter the firmware, boot loader, and boot verifier code loaded from secondary storage. The attacker is assumed to not be able to make hardware modifications undetectable to inspection, including overclocking and installation of transmitters to offload the hashing problem. This is for local (non-remote) attestation only. We have written a prototype for a non-SMP x86 computer and tested problem parameters that produce timing detectable results under a hypervisor/virtualizer and assess if these parameters are feasible for practical use.
Mark is a Winnipeg based information technology contractor, B.C.Sc, and LFCS. Mark spoke at BSides Winnipeg 2013.
Interactions Between Deep Freeze and Active Directory
Meako Marlow
This talk will discuss Meako's experience with supporting labs and classrooms at a University using Deep Freeze and joining Active Directory. It will cover the challenges involved and things to be aware of.
Meako currently works at the University of Manitoba with their desk-side team. His talk will be based on experiences from working at the University of Winnipeg.
Detecting and Preventing Phishing Attacks with DNS Reconnaissance
Mike Saunders
Anthem and Premera Blue Cross Blue Shield are just two examples of recent high-profile attacks that had roots pointing to phishing attacks and DNS typosquatting. In this talk, we’ll discuss what typosquatting is and how these attacks can be detected and prevented and demonstrate a tool that can be used to automate monitoring for these attacks.
Mike is a penetration tester with a heart for defense. He has presented at BSidesMSP (3x), the North Dakota IT Symposium (3x), the NDSU CyberSecurity Conference, and has presented this talk at DerbyCon 2015.
Privacy in Data Management
Noman Mohammed
Big data is the fuel of modern economy. It allows us to do better urban planning, combat new diseases, ensure national security, and has become the driving force behind innovation, productivity, and growth. All these new possibilities are enabled by new technologies that are capable of storing, integrating, and analyzing all sorts of digital breadcrumbs that we leave behind in this information age. On one hand, the collected data offers tremendous opportunities for mining useful information. On the other hand, the mining process poses a threat to individual privacy since the collected data often contains sensitive information. The current practice in data sharing relies primarily on policies and guidelines on the types of data that can be shared and agreements on the use of shared data. This approach alone may lead to excessive data distortion or insufficient protection. This talk will present the recent research results that try to find a right balance between the privacy protection and big data rewards. In particular, this talk will explain different definitions of privacy model, show their limitations, describe some algorithms to enforce them, and discuss open problems for future research.
Noman received a Ph.D. degree in Computer Science from Concordia University in 2012. He is currently an Assistant Professor in the Department of Computer Science at University of Manitoba, Manitoba, Canada. Before coming to UofM, he was an NSERC postdoctoral fellow in the School of Computer Science at McGill University and a member of the Cryptography, Security, & Privacy (CrySP) Research Group at the University of Waterloo. His research interests include private data sharing, privacy-preserving data mining, secure distributed systems, and applied cryptography. He has received several prestigious awards including the Best Student Paper Award in ACM SIGKDD International Conference on Knowledge Discovery and Data Mining, 2009, NSERC postdoctoral fellowship, and Alexander Graham Bell Canada Graduate Scholarship (NSERC CGS).
The Challenges of System/Network Segmentation in an Enterprise
Oleksiy Vasylyuk
The design and implementation of network and system segmentation in medium to large environments can be challenging as there appears to be no common approach for implementation and communication of segmentation to technical and business units. This talk will describe the challenges of such implementation and summarize the potential solutions for physical and logical alignment, and its socialization. The material presented will be based on recent and ongoing experience with designing, implementing, and communicating network and system segmentation via numerous hands-on table top exercises, and analysis of numerous literature sources.
Oleksiy is an information security geek with a Computer Science degree, and various IT certs.
Modern TLS in the Enterprise
Sean Cody
The state of TLS/SSL is changing at a rapid pace over the last year and its use and implementation is being dragged around by the ear by the browser vendors. What are the consequences of implementing modern TLS in complicated and regulated environments? How has TLS been used in these environments to date? How do we design services which implement all of the benefits of TLS but also limit their impact to infrastructure and regulatory costs? Are TLS and PKI strategies identical and aligned across application stacks and portfolios? This talk will give examples of the ways TLS has been used in Enterprise infrastructure over the years and will discuss possible solutions and strategies to meld the seemingly incompatible requirements of regulatory compliance and end-to-end security.
Sean is an Infrastructure Specialist at The Great-West Life Assurance Company with a B.Sc. in Computer Science. He worked in the ISP and Visual Effects spaces before moving on to Enterprise IT.
BGP, some Python, and a DB
Theodore Baschak
How do services like BGPmon and Dyn provide Internet Intelligence? This talk will describe the process of building a small-scale BGP update logger, running it on a single AS, and then attempt to scale it up.
Theodore is an Internet routing guru, and an avid open source documentation contributor.
Let Go of the Tools
Tim Jensen
Information Security training is often taught using common toolsets and how to interpret the output. The majority of Web application findings are not caught by common toolsets in use today. This talk is targeted at new to mid-level penetration testers and will show examples of real world programming logic failures and how to exploit them.
Tim is a Senior Penetration Tester from Fargo, North Dakota. He specializes in Web application and network penetration testing. Tim ran a hacklab/penetration testing training program for four years in Fargo. He have over 1,000 hours experience teaching penetration testing.
Network Configuration Management
Zoë Rose
Configuration Management is important because any changes made can have a huge impact on your network. This talk will be discuss the importance of change management, specifically configuration management of routers and switches. The goal is to give more visibility into large networks with automated tasks. Zoë has created a script for auditing logins, daily configuration changes, and snapshots.
Zoë is an inquisitive, hard-working networking professional who is constantly learning and tackling new challenges. She is known to many as a protector of networks and a cuddler of ferrets. Some have even called her an Internet superhero.